Brazil should just ban Tesla from being sold in their country. They would have a pretty big market I’d imagine
EVs have a market share of about 5% in Brazil, apparently.
I’d be shocked if anyone didn’t assume they’d do this.
Great 6 part pod on ai that I’ve found really interesting and entertaining.
Tech journo clones his voice and hooks it into ai and unleashes it on escalating ways on the world. They process was fascinating and the results are fantastic/unhinged/terrifying/hilarous all in one!
On a similar topic, anyone looking to learn more about how LLMs/GPTs work might want to check out 3Blue1Brown on YouTube.
The Neural Networks course is surprisingly approachable for the average Joe without too much brain-breaking mathematics concepts, and even if you don’t completely understand everything (which I certainly don’t), you will come away with at least a basic intuition (or approximation) for what’s going on inside the model.
It definitely feels a lot less voodoo to me now than it did before.
7 chapters, each a nice bite size 10-30mins.
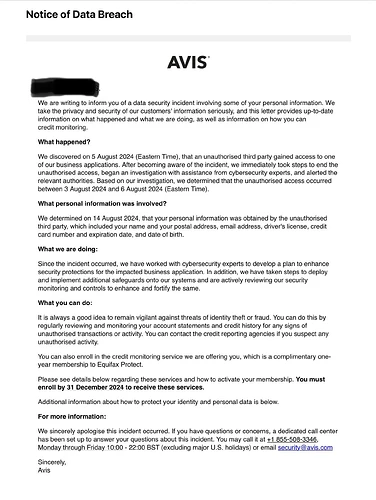
Quality breach at Avis.
Name
Address
Email
Drivers licence
Credit Card number & Expiration
DOB
I’ve hired a car from them this year but haven’t got an email yet. Wonder how wide this was.
It’s lucky they didn’t get that much information.
Damn that’s pretty bad. They will cop a lot of flak for this I hope
I’ve said it before, time to start really making it hurt for businesses that don’t protect customer PII, huge fines and withdrawal of rights to hold PII for repeat offenders.
So stupid question, assuming to take human stupidity out of the equation (unlocked computers, bad passwords etc.) is any data actually safe, no matter how well it’s protected? I once spoke to a guy who did drug testing for athletes. He said it was a cat and mouse game, someone comes up with a new drug, they learn how to detect it and then someone comes up with a new drug… rinse repeat. Is the IT sector essentially the same? Security increase, someone comes up with a way to defeat it etc etc.
It’s always about risk minimisation and mitigation.
It’s not necessarily about new threats (not the data side afaik) it’s more a balance between security, cost, and usability (efficiency as the business would see it).
Good hackers are always going to be one or two steps in front of the latest security technology. Who do you think makes it?
There’s a reason why organisations like the NSA recruit high-level hackers.
But I’m assuming most of risk minimisation would revolve around the human aspect? Are basic security systems and encryption at the point where the only ways to really get through either by brute force, or because Janet f*cked up and opened up the wrong email
To hack people, one would think.
Only partially. A huge chunk would be around data management.
E.g.
- What should be/needs to be encrypted vs what can be clear.
- What datasets must be stored separately for security purposes (and not just for data break security but for fraud control etc) - e.g. Credit card details and account details…
- What they must purge according to privacy laws etc.
- IP security
That’s all balanced against what they want…
- Maximise exploitation/return on the investment (data collection & storage costs, opportunity costs)
- Minimise operational overheads (storage, data security, data management costs, agility restraints)
From what I’ve read and heard from the security types I know most breaches are:
a) someone fucked up and left something unsecured (e.g. Optus)
b) someone fucked up and gave access to someone they shouldn’t have (phishing/spear phishing attacks etc)
c) third party fuck ups (vendors being given data for project or services and being stung by a or b).
d) inside job (seemingly far more rare than the others)
The “new threat” stuff seems to typically be how the extortion part works. For example ransomware attacks that encrypted data in situ became big and were a major threat because institutions had really poor backup procedures (and disaster recovery capabilities). Once that attack becomes/became less viable then they move onto data extraction and threats to sell the data directly to an interested party or public release.
It’s a question for each organisation. In the past, I walked in to work for some organisations that had no encryption on personal data whatsoever. It wouldn’t surprise me if there are many Australian organisations that were, and still are, the same. It would also not surprise me if many organisations just thought that putting a single method of encryption was enough to safeguard their systems. There are websites which can freely decrypt bodies of text these days.
To put it in simpler terms, I.T. security need to make sure the proverbial car is locked down tight. There are enough methods to deter 99% of people or other organisations from just opening the proverbial car door. I just think most Australian businesses are either incredibly lazy, or plain don’t want to be informed about the risks they’re taking. This is why jubal’s call for bigger penalties is extremely important. Big business in particular will be made to care about this sort of thing.
To be clear. My issue is with organisations which fail in their duty of care to secure PII.
90% of corporate PII data breaches are due to negligence, parsimony or laziness.
While IT security is very much an arms race, every client I’ve had in the past 20 years, including 3 Federal Government departments, 4 State Government Departments, 5 or 6 household name global corporations and half the major banks and insurance businesses in Australia, every one of which held and managed extensive PII, had clear, obvious and imminent risks around their handling of PII ranging from not patching devices and software to maintain security to allowing unobfuscated PII to be used in testing environments.
Every single organisation knew about their issues, every single one of them either
- Ignored the issues because the people responsible couldn’t be arsed
- Chose not to address the issues because it would 'cost them too much money
- Pretended the issue didn’t exist because it would make them look bad
Organisations who do not take the protection of PII seriously and take all reasonable precautions to protect it (there are plenty of compliance standards that balance risk with effort, like IRAP) simply should not be allowed to hold that kind of data.
In other words the right to collect, use and retain PII should be licensed against suitable capability and performance and the types of breeches caused by the things I described should be punished with sanctions up to and including the loss of license to have and use PII.
Clarity - PII is Personally Identifiable Information like email address, Tax File number, Drivers License image etc.
I’m not sure just how comfortable I am with the interviewing of dead people.
Wow, how does it stay so up to date with current events!